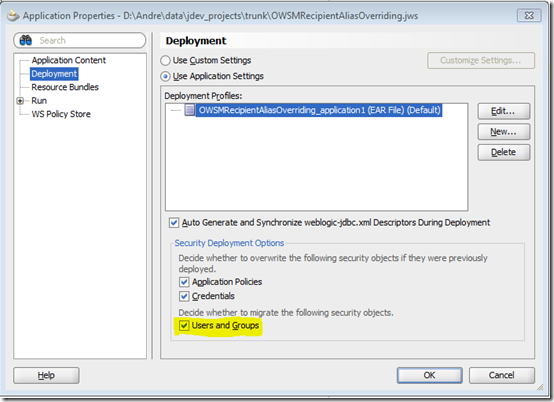
When you run an ADF web application directly from JDeveloper, it starts its embedded WLS and deploys the application. In such context, JDeveloper has a very convenient feature when dealing with users and groups defined in the application's jazn-data.xml file. They get deployed along with the application into WLS embedded LDAP server, provided the Users and Groups check box is selected in the Application Properties Deployment window, as shown right below:
Then by simply asking JDeveloper to run your application you get everything you need.
As said, that's a JDeveloper convenience that only works when deploying the application through JDeveloper. Do notice this apply whether you click & run a page or taskflow or explicitly ask JDeveloper to deploy your application into WLS, as shown:
But if you’re not using JDeveloper, you’re on your own. You should not expect it to happen when generating an ear file and deploying via any other means, although jazn-data.xml is packed within the ear file. `I've gotten this question from a few of customers. And some believe that's a bug. It's not.
You need to manually populate WLS embedded LDAP. There are two ways to accomplish it:
1) Using wlst.sh:
> connect ('weblogic','<weblogic-password>','t3://<server>:<port>') > cd('<folder-where-your-ldif-file-is-kept>')> > cmo.importData('DefaultAtn', '<your-ldif-file>', None)
2) Using WLS Console:
Notice the path at the top to understand how to get to this screen.
Enter the ldif file absolute path name in “Import File” on Server field. Notice the file has to be accessible on the server file system.

Here's a small sample of the ldif file you can use and extend:
dn: dc=@domain@
dc: @domain@
objectclass: top
objectclass: domain
dn: ou=@realm@,dc=@domain@
ou: @realm@
objectclass: top
objectclass: organizationalUnit
dn: ou=groups,ou=@realm@,dc=@domain@
ou: groups
objectclass: organizationalUnit
objectclass: top
dn: cn=group1, ou=groups, ou=@realm@, dc=@domain@
memberURL: ldap:///ou=people,ou=@realm@,dc=@domain@??sub?(&(objectClass=person)(wlsMemberOf=cn=group1,ou=groups,ou=@realm@,dc=@domain@)) objectclass: top
objectclass: groupOfUniqueNames
objectclass: groupOfURLs
cn: group1
uniquemember: cn=user1,ou=people,ou=@realm@,dc=@domain@
dn: ou=people,ou=@realm@,dc=@domain@
ou: people
objectclass: organizationalUnit
objectclass: top
dn: uid=user1,ou=people,ou=@realm@,dc=@domain@
objectclass: top
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
objectclass: wlsUser
cn: user1
sn: user1
uid: user1
userpassword: welcome1
wlsMemberOf: cn=group1,ou=groups,ou=@realm@,dc=@domain@